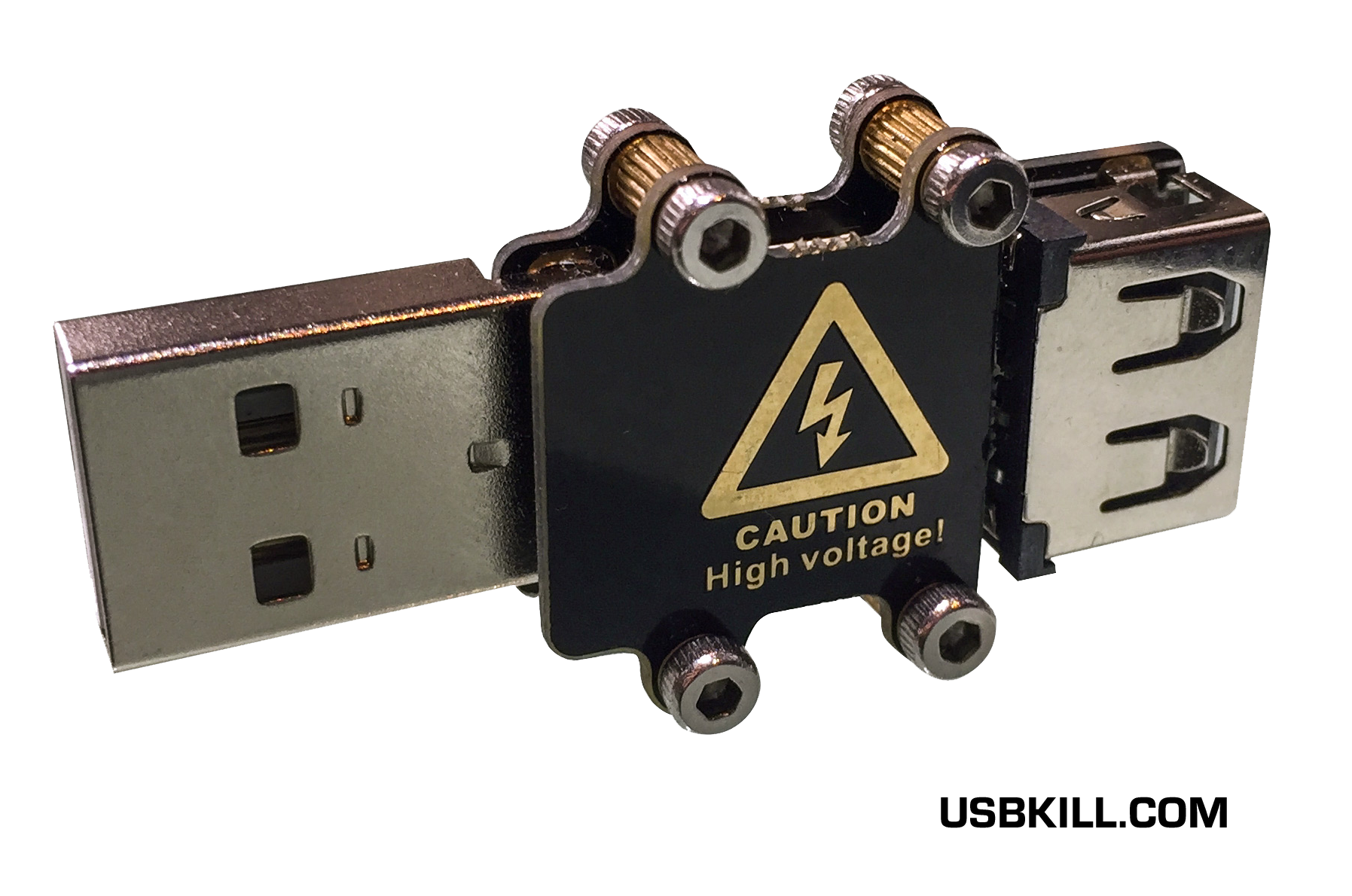
A Hong Kong-based technology manufacturer, USBKill.com, has taken data security to the “Mission Impossible” extreme by creating a USB stick that uses an electrical discharge to fry an unauthorized computer into which it’s plugged.
“When the USB Kill stick is plugged in, it rapidly charges its capacitors from the USB power supply, and then discharges – all in the matter of seconds,” the company said in a news release. The USB Kill 2.0 stick.
To do that, the USB stick discharges 200 volts DC over the data lines of the host device. This charge/discharge cycle is repeated many times per second, until the USB Kill stick is removed.
The company said its USB Kill 2.0 stick was created to test against “power surge attacks” and to prevent data theft via “juice jacking.”
Juice jacking is a form of cyber-attack enabled by malware on a computer that surreptitiously copies data from a mobile device that’s using a USB charging port that also doubles as a data connection.
The company also sells a USB Protection Shield that’s designed to allow testing of the USB Killer while protecting the host machine. The USB Kill 2.0 stick retails for around $56 and the Test Shield will run an additional about $15.70.
While the USB Kill 2.0 stick has been “designed and tested to be safe,” the company warns that it “is a high-voltage device – it is not a toy – and is only intended for responsible adults.”
To ensure this, USBKill.com “strongly condemns malicious use of its products.”
“When tested on computers, the device is not designed or intended to erase data. However, depending on the hardware configuration (SSD vs platter HDD), the drive controllers may be damaged to the point that data retrieval is impractical,” the company said in its marketing material.
An internal look at the USB Kill 2.0 device.
USB Kill also said the device was created for use by hardware designers of public machines, such as photo booths, copy machines, airline entertainment systems and ticket terminals — anything with exposed USB ports that need to “ensure that their systems resist electrical attacks.”
“Finally, the general public, or anyone who wants to test or kill their own devices should equip themselves,” the company stated. “Penetration testers and security auditors should include the USB kill 2.0 to their arsenal of testing tools.”
The company claims its own tests revealed more than 95% of computer devices are affected by a USB power surge attack, and almost all consumer-level hardware fails when tested against the USB Kill. The most frequent outcome, the company admits, is the complete destruction of the device (i.e., laptops, televisions, smartphones, etc).
“Almost all consumer-level hardware fails when tested against the USB Kill,” the company states; the only exception so far appears to be “latest version of Apple’s MacBook, which has surge-protected USB ports.
Senior Reporter Lucas Mearian covers financial services IT (including blockchain), healthcare IT and enterprise mobile issues (including mobility management, security, hardware and apps).